Software Supply Chain Security Terms
Tuesday, February 6th, 2024
The world of “Software Supply Chain Security” can be overwhelming, murky, and unclear. To help clarify my own thinking and organize what I’m seeing out there, I’ve put together the following cheat sheet on terminology and descriptions.
I’ve also included a short list of resources including blog posts, talks, and podcasts from industry experts on the topic.
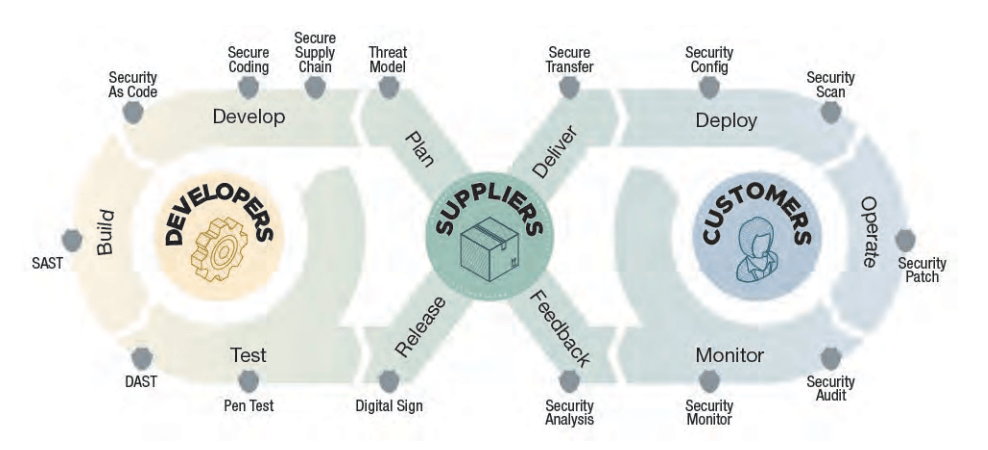
Software Supply Chain Security: The process of identifying & protecting against risks involved in the end to end creation and deployment of of software. This is a expanded and more holistic view of potential risks vs. the traditional definition of application security which was focused on the first party code that a company’s developers wrote.
Some examples of the types of things that Software Supply Chain Security encompasses include (but is not limited too):
The integrity of the software build process including CI/CD pipelines.
The integrity of source code repos.
The integrity of software dependencies including libraries, frameworks, modules, etc.
The integrity of any third party software being used in the enterprise.
Integrity of first party code developers are writing.
Integrity of container images being used.
Google’s SLSA: A open source framework created by Google & other industry leaders that provides guidance on how software providers can harden their supply chain security. The scope of the frame work is focused on:
Source Code Integrity
Build Integrity
Availability
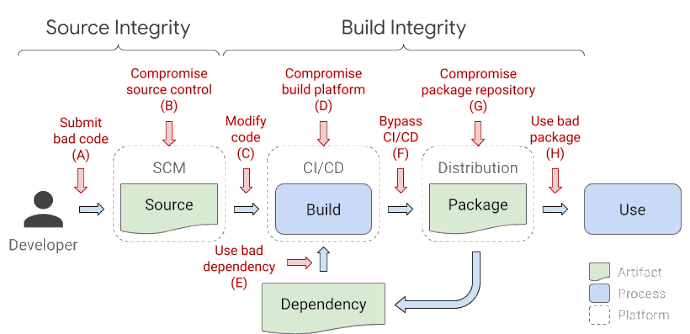
Google SLSA Threat Framework
NIST Secure Software Development Framework (SSDF): A set of guidelines created by the National Institute of Standards & Technology (NIST) that provides guidances on building security into the entire software development process.
The framework is organized in the following way:
Prepare the Organization (PO): guidance on policies, procedures, and tools.
Protect the Software (PS): guidance on ensure integrity of code, dependencies, and sensitive data.
Produce Well-Secure Software (PW): guidance on integrating security into development process such as threat modeling, risk assessments, secure coding, testing, etc.
Respond to Vulnerability Reports (RV): guidance on mechanisms to respond to vulnerabilities identified in software products.
SolarWinds Hack: In September 2019, The Russian Intelligence Service added a malicious backdoor to the code of the SolarWind’s Orion tool. They did this by adding 3,500 lines of code during the compiling process so that it was not noticed. SolarWind’s had thousands of customers who deployed this code during a routine update leading to the compromise of approximately 100 companies and a dozen government agencies including Microsoft, Intel, Cisco; the Treasury, the Justice and Energy departments and the Pentagon.
Log4J Hack: In December 2021, attackers discovered a critical zero day security vulnerability in the Apache Log4j library, which is a logging utility software component commonly used in Java applications and cloud services. The flaw allowed attackers to gain remote code execution which is a complete takeover of the system through sending malicious inputs. This enabled attackers to steal data, install malware, and get further compromise of networks.
Kaseya Hack: In July 2021, a Russian ransomeware group exploited a vulnerability in Kaseya’s VSA software which resulted in compromise of IT managed services companies and 800-1500 of their end customers who were small and medium sized business undergoing a ransomeware attack. Essentially these small businesses had no way of knowing they were vulnerable as the issue happened farther up to the chain of software being used.
White House Executive Order on Improving the Nation’s Cybersecurity (EO 14028): In May 2021, in response to these types of attacks, the White House established new requirements to secure the federal government’s software supply chain. These requirements involve systematic reviews, process improvements, and security standards for both software suppliers and developers, in addition to customers who acquire software for the Federal Government. This was important as it created a roadmap for the public sector but also shaped the discussion in the private sector around best practices.
Software Bill of Materials (SBOM): Is a list of all the open-source and third-party components present in a software’s code. An SBOM lists the component licenses, the versions of the components used in the code, and their patch status, which allows for quick identification of any security or license risk. Software vendors are providing SBOMs to their end customers for full transparency of what is in their product and software consumers are requesting SBOMs and storing, organizing, and evaluating them for security risks.
Open Software Supply Chain Attack Reference (OSC&R): A open framework that gives a systematic way to understand attacker behaviors and techniques. It’s organized like the MITRE ATT&CK framework, with a structured view of the tactics, techniques, and procedures (TTPs) used by adversaries.
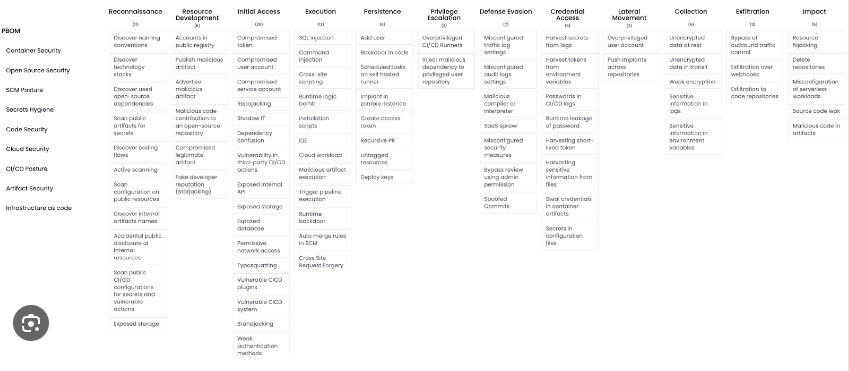
OSC&R Framework
Vulnerability Exploitability Exchange (VEX): information provided along with a SBOM that explains whether a vulnerability in a component used by the software is actually exploitable or not. This additional context is helpful to software consumers as it helps them understand the vulnerability details, exploitability, and detailed analysis. It also tells them what actions the vendor has taken, or which the consumer must take, to reduce risk.
Software Identification (SWID) Tagging: A way for organizations to track the software installed. SWID Tag files contain descriptive information about a specific release of a software product. Some teams use this as part of a asset inventory & management processes, as well as it is used to verify the software integrity.
Cybersecurity & Infrastructure Security Agency (CISA): the lead for government agency for federal cybersecurity and the national coordinator for critical infrastructure security and resilience. Led by Director Jen Easterly, it has 3,000+ employees and a annual budget of $2.9B, CISA works across the entire federal government and partners with the private market.

